Researchers discovered that hackers can turn your own phone into a sonar snooping device to steal your phone unlock pattern
We often take for granted just how much technology is crammed into our tiny smartphones. Modern phones have all sorts of sensors and gyros that allow them to know exactly where they are, which way they’re facing, and even how fast they’re moving in a particular direction. Even the most basic tech, that enables our phones to record and transmit our voices and receive and play the voices of others can detect and play sounds outside the realms of human hearing.
Are you using productivity apps correctly? sam.cmd.push(function() { sam.display('see-through-article-page-desktop'); }); Read about some common mistakes

Are you using productivity apps correctly?
Unfortunately for us, even though these highly tuned instruments turn our smartphones into the digital equivalent of a Swiss army knife, they also offer hackers numerous ways into our most private digital lives. Researchers in Sweden and the UK unearthed a new ingenious way that hackers can exploit the tech we take for granted.
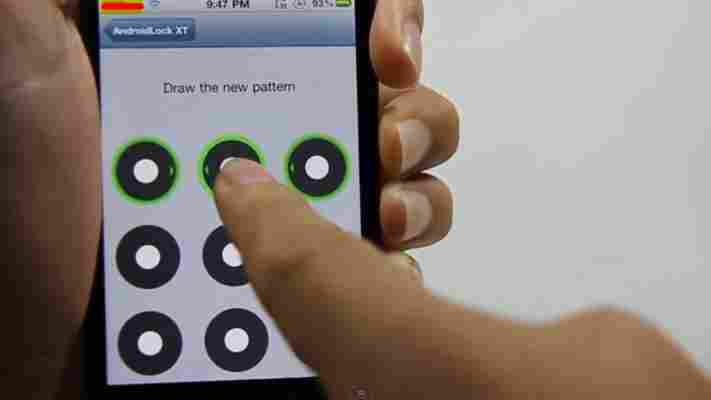
SonarSnoop uses the basic speaker and microphone setup found on all smartphones and uses it to track a finger’s position as it moves across a screen. Used in the right way, this could track that finger as it inputs the security lock pattern used on most Android smartphones.
The vulnerability uses an innovative new tech that was designed as a control method for smaller interactive devices like smartwatches. FingerIO was released back in March 2016 and uses a system similar to sonar to track movement and then relay that movement as a form of control to the device. It is particularly useful for devices with small touchscreens.
SonarSnoop takes FingerIO and uses it to break into smartphones. A lot of phones these days are coming with fingerprint sensors but there are still millions of devices out there that use an unlock pattern to secure them. If your phone still uses an unlock pattern it could be vulnerable to SonarSnoop.
To protect against a potential SonarSnoop attack it is important to only download apps from reputable app stores like Google Play or here at Softonic. The malicious code could be found in app APK files found on less reputable third-party download sites. Once the code is installed on your device it will be very difficult to detect and remove. You want to keep SonarSnoop off your device in the first place.
For more tips on keeping your mobile free from viruses and malware check out some of our mobile security tutorials below:
More Softonic Articles
5 tips to prevent security issues with your phone ►
8 tricks to strengthen your WhatsApp security ►
7 mistakes that put your internet security at risk ►
8 tricks to boost your security on Google Chrome ►
The researchers investigated the use of SonarSnoop on a Samsung Galaxy S4 running Android 5.01. They discovered that the use of the attack was able to hone in on the correct unlock pattern 70% of the time , but stressed that they expect this accuracy to improve over time. They were also keen to point out that SonarSnoop could also work on other devices that sport a microphone and speaker setup.
If you’d like to read up on SonarSnoop in greater detail you can find the research paper co-authored at the Lancaster University in the UK and Linköping University in Sweden here .
